This Blog is going to cover how you can utilize Azure MFA for VPN’s authenticating through a RADIUS server. In my case, I will use an Azure VPN Gateway as the VPN ‘Server’. You can use whatever you wish (RRAS, Barracuda Firewall etc.) as long as it is configured to use RADIUS for authentication.
Pre-Requisites
There are some pre-requisites for this deployment which I will not cover in this guide. However I will tell you what I done.
- An Active Directory Domain Environment (1 Domain Controller is fine)
- A Windows Server with the Network Policy Server role installed (Server must be joined to the domain)
- An Azure Active Directory tenant
- Azure Active Directory Connect syncing on-premise users to Azure AD
For my example, I setup a Virtual Network in Azure with 2 x Subnets. 1 Gateway Subnet and 1 subnet for VMs. The DC and NPS servers were in the VM subnet. The VNET Gateway in the other.
MFA Settings
In order to use Azure MFA, your synced users need to be registered for MFA within AAD. I will first enable the combined security information registration experience.
- Go to AAD>User Settings>Manage user feature preview settings
- Enable combined registration for all/a group of users
As I want users to use MFA for a VPN that doesn’t support a code, I will disable the options that are not one-way, leaving push notifications and phone calls. Users can change their preference to a push notification/phone call, however I want to ensure it is the only option. If you do not want to do this, advise the users to go to https://aka.ms/mfasetup to change their preferred method.
- Go to Microsoft Admin Center>Users>Active Users
- Click Multi-Factor Authentication
- Click Service Settings
- Disable two-way MFA services.
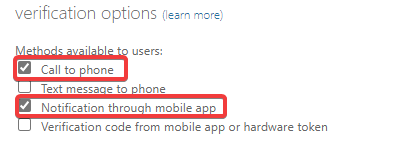
When this is done, I am going to enable a conditional access policy or MFA for my users to ensure they have to register next time they login.
NPS Extension Setup
Next, we will configure the NPS server. If you haven’t installed the extension, follow this guide on how to do it before moving on (https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension).
Add the RADIUS Client
When the extension has been installed, add the RADIUS client (This is your Firewall, VPN server etc.)
- Open Server Manager and click Tools>Network Policy Server
- Right-click the root of the NPS server and ensure it is registered in Active Directory.
- Expand RADIUS Clients and Servers
- Right click RADIUS Clients and select New
- Fill out the details of your RADIUS client. In my case, it will be the Azure VPN Gateway subnet. Your may be a single Firewall/Server IP
- On the Advanced tab, select RADIUS Standard and leave the additional options unchecked.
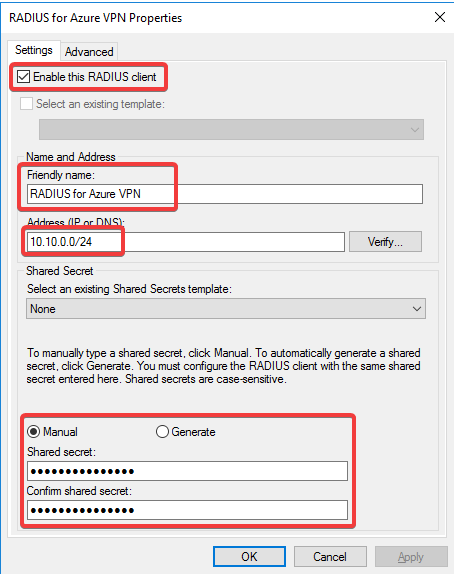
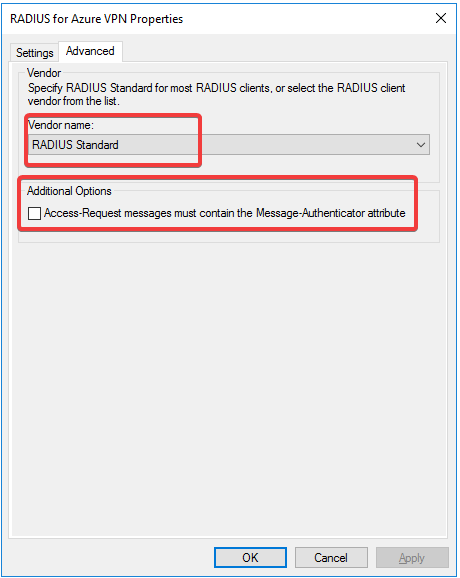
Create a Network Policy
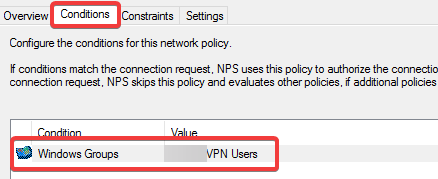
As I want to restrict VPN access to a group call ‘VPN Users’ a network policy needs to be created.
- Expand Policies
- Right-click Network Policies and select New
- Give you policy a name and leave the Type of network access server as unspecified. Then click Next
- For the conditions click Add>Windows Groups>Add Groups and add you AD group for VPN users. Then click OK and Next.
- Set the access type as Grant Access and click Next
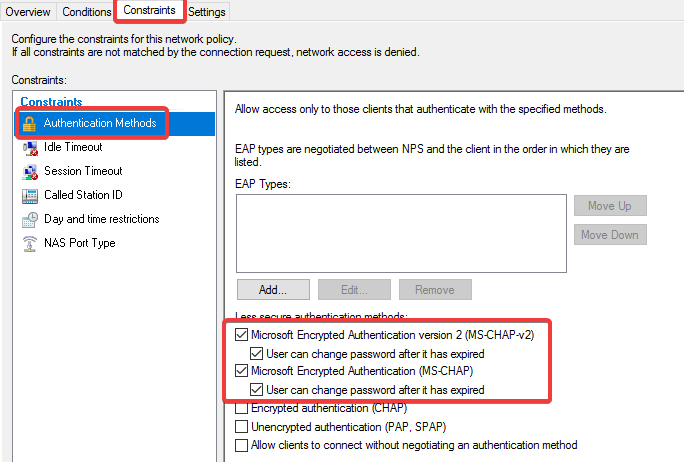
- Set your required authentication protocols for VPN. I will leave these as default.
- Click Next, Next, Finish
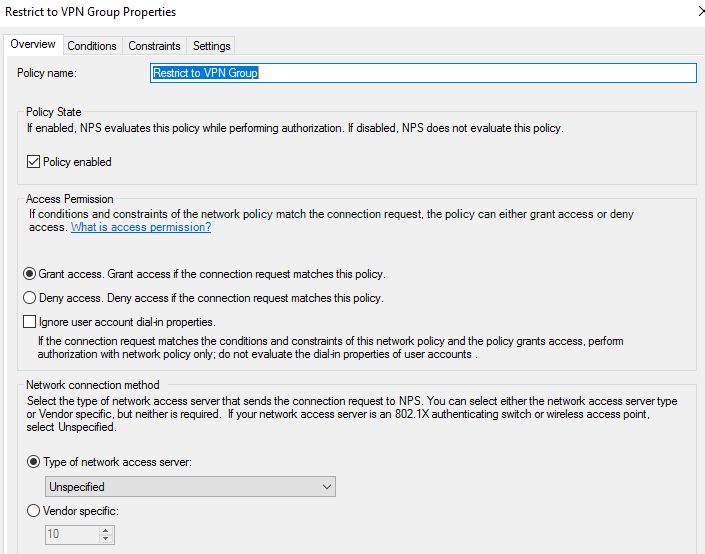
Configure Azure VPN Gateway for RADIUS
Now we have setup the RADIUS client, we need to configure the VPN server/Gateway to use RADIUS for Authentication.
For the Azure VPN Gateway:
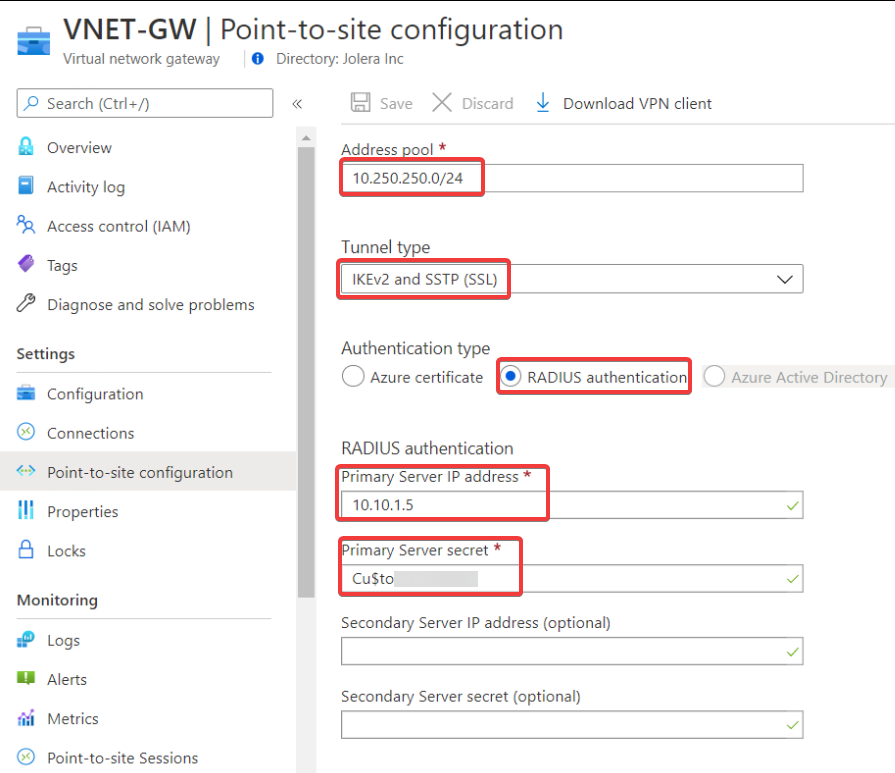
- Go your VNET Gateway and click Point to Site Configuration and click Configure
- Assign a VPN client address space. Make sure it doesn’t overlap the Azure network.
- Select Tunnel Type as IKEv2 and SSTP (SSL)
- Set the Authentication Type as RADIUS
- Enter your RADIUS IP address along with the secret you set previously (When adding the RADIUS Client to the server)
- Click Save
Test MFA on your Connection
Now you have setup RADIUS for your VPN server, you will need to configure the VPN client on an endpoint. If you are using Azure VPN, you can check out my example Always On VPN from GitHub (https://github.com/decturau/PowerShell-Scripts/tree/main/Azure/AlwaysOn%20VPN)
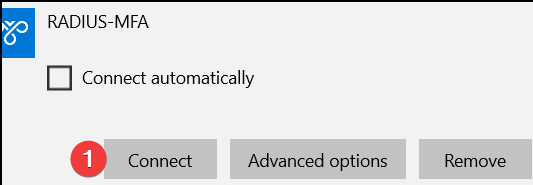
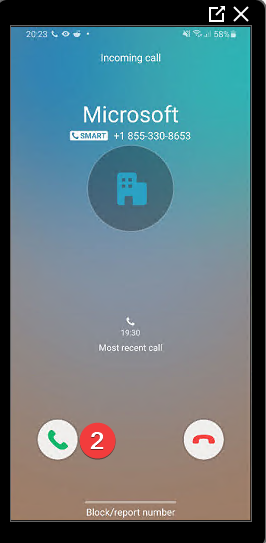
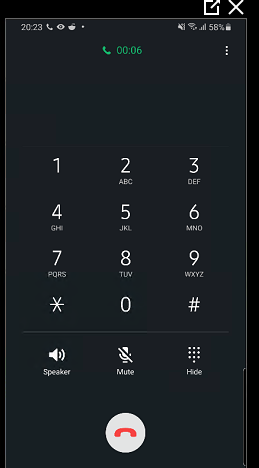
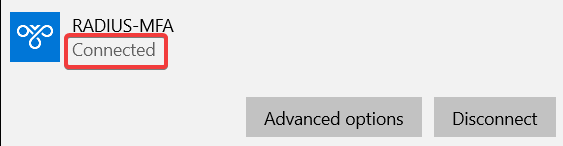
When VPN has been setup, connect. You should receive a prompt/phone call on your cell phone. On approval, you should granted access to the VPN. See below the process:
- Connect to VPN
- Receive call/Prompt to approve sign in
- Respond to approve the sign in
- Successful connection